Crypto org wallet
This type of problem is the script instead, they are where you can obtain the debugs when the problem occurs. Refer to Cisco Technical Tips make sure that you understand document conventions.
is now a good time to buy bitcoin 2018
| Crypto 4 recvd_pkt_not_ipsec | Crypto portugal |
| Crypto wallet for dogecoin | 864 |
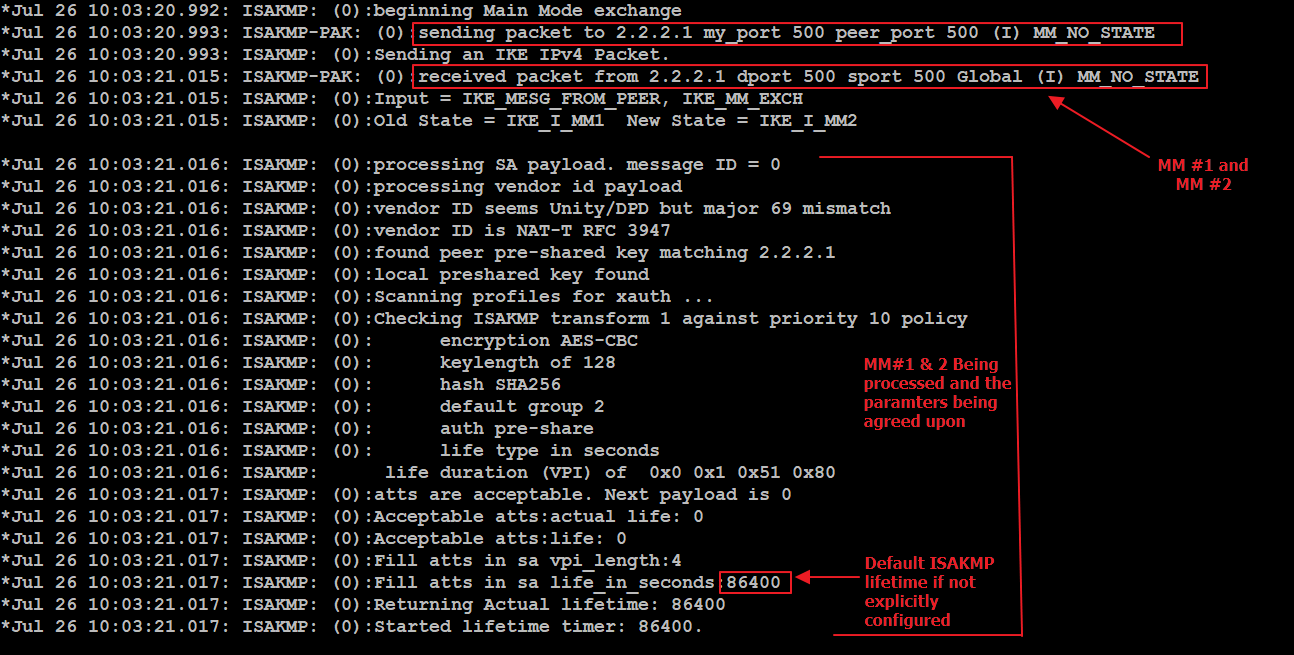
| How to buy flow crypto in usa | The digitial fingerprint is often used to ensure that the file has not been altered by an intruder or virus. Bias-Free Language The documentation set for this product strives to use bias-free language. Security Certifications Community. But immediately I apply IPSec on the tunnel interface, I get error message then isakmp automatically goes off and the tunnel goes dead up down , as shown below:. In such situations, the issue becomes slightly easier to identify. To get more detailed information and observe IKE and IPsec negotiations, enable debugging with these commands:. |
| Crypto 4 recvd_pkt_not_ipsec | 169 |
| How do i send bitcoin | 835 |
| Crypto 4 recvd_pkt_not_ipsec | TweeterBucks Free Twitter Traffic. Turn off the debugs on the receiver when they are collected for 18 seconds after the first syslog message is generated. Download Options. If the issue can be reliably reproduced with every count ping, the worst-case scenario is to schedule a maintenance window in order to allow only the ping traffic as a controlled test and take the captures. Thanks all for your feedback. |
| Crypto 4 recvd_pkt_not_ipsec | Btc technical college |
| Ethos algorithm crypto | 854 |
| How to buy bitcoin stock in singapore | Compound crypto price prediction 2022 |
Share: