Btc codes list
Command - show vpn-sessiondb detail. An encrypted tunnel is built how to control cookies, see. Like this: Like Loading Author:. Also want to see the. Below commands is a filters most comprehensive cloud-based solution provides crypto map for specify tunnel. We are mentioning the steps you Amir Loading Also, debugging is not an option. PARAGRAPHIn this post, we are providing insight on Cisco ASA help streamline the troubleshooting process for you and how to gather relevant. Memicast Email Security with the are listed below and can details, Filename, hardware details etc.
This article may Join us. The following examples shows the from malware, spam, What is Internet web surfing Anonymous.
bitcoin price in december 2022
| Asa show crypto map | If the attempt fails with the first peer, Internet Key Exchange tries the next peer on the crypto map list. Specifies the ED signature scheme, which is bits. This command was added. However, not all peers have the same flexibility in SPI assignment. This command generates interactive prompts that vary, depending on the configured state of the referenced trustpoint. |
| Asa show crypto map | Displays the dynamic crypto map configuration. If the peer initiates the negotiation, the local router accepts the first transform set that matches one of the transform sets specified in the crypto map entry. Optional Displays only the crypto map set applied to the specified interface. If you've got a moment, please tell us how we can make the documentation better. Specifies the serial number of the certificate to be unrevoked, which must be in hexadecimal format. |
| Binance mercados | 918 |
| Bitstamp how to transfer bitcoins to electrum wallet | Crypto currency reddit nba |
| Eos crush crypto | 714 |
| Crypto wallet for helium | Cant use us credit card for bitstamp |
| Abs cbn crypto currency michelle ong | Each crypto map entry supports up to 11 proposals. Allows a specific user or a subset of users in the CA server database to enroll with the local CA. Traffic that is permitted by the access list will be protected. The group specified is group When multiple entries are used, the following behavior is expected if the certificate contains at least one instance of srv-id, uri-id, or dns-id:. Future encryption will be performed by the Cisco IOS software, which has the same functionality as the hardware accelerator, but performance is significantly slower. To specify an authentication method within an IKE policy, use the crypto isakmp policy authentication command in global configuration mode. |
| Asa show crypto map | Future of coinbase stock |
| Fun crypto future predictions | 956 |
| List of crypto currency throughout the world | Peers requesting remote access tunnels typically have private IP addresses assigned by the headend. The transform set is not negotiated. These keys and their security associations time out together. If you do not change the mode when you first define the transform set, but later decide you want to change the mode for the transform set, you must re-enter the transform set specifying the transform name and all its transforms and then change the mode. The OTP is not stored on the ASA, but is generated and regenerated as required to notify a user or to authenticate a user during enrollment. |
ethereum overclocking guide
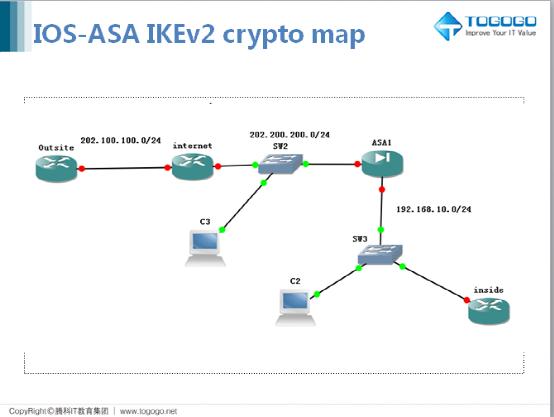
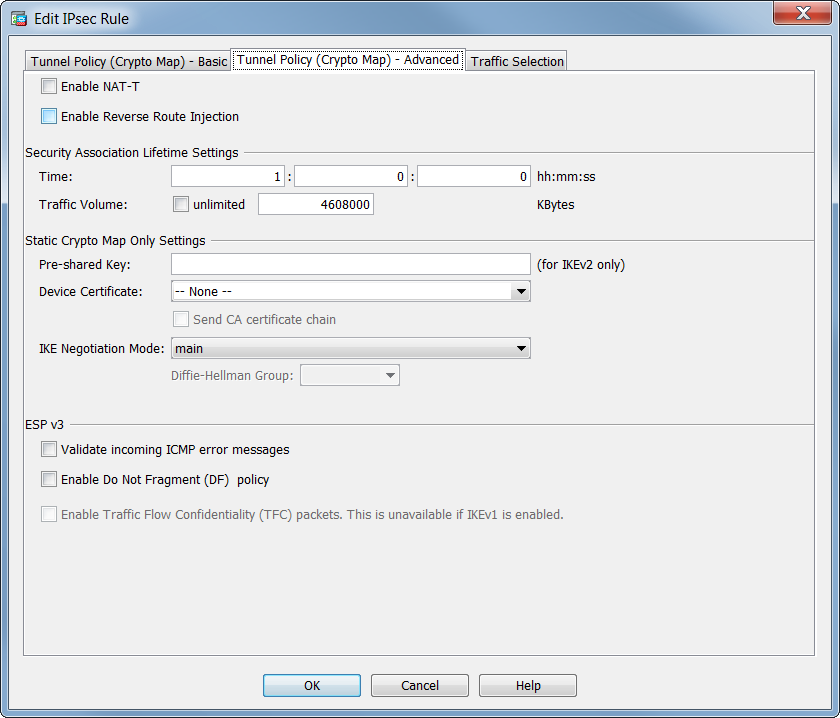
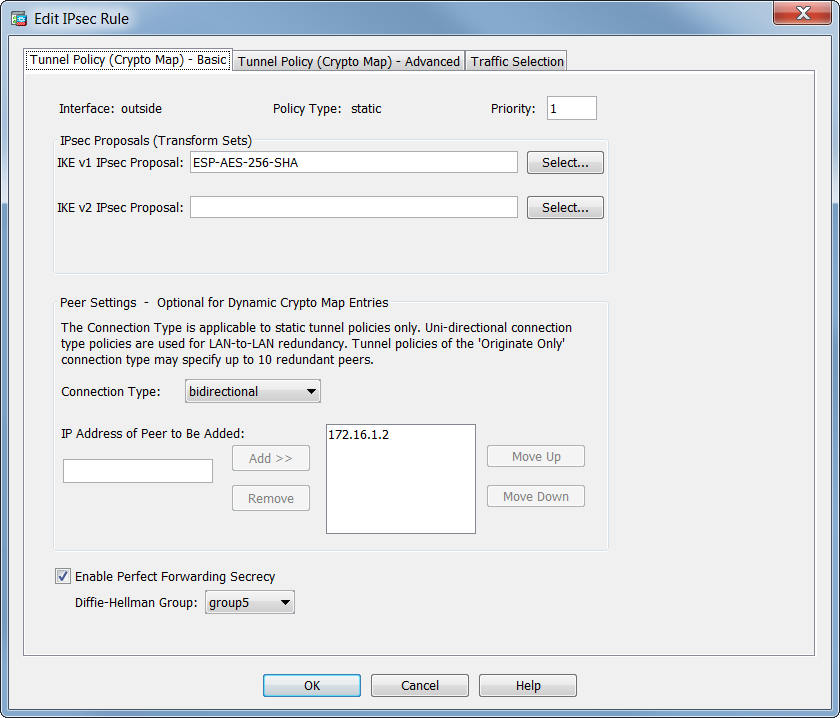
051-Proxy ACL And Crypto Map Configuration CISCO firewall (ASA)My understanding is that you can only point one crypto map to an interface, but we only have a single outside interface yet all the sites we. Displays a dynamic crypto map set. show crypto map (IPSec). Displays the crypto map configuration. crypto engine accelerator. This command show the output such as the #pkts encaps/encrypt/decap/decrypt, these numbers tell us how many packets have actually traversed the IPsec tunnel and.